Protecting the crown jewels of your business application should be all about layering up the protection.

Before any traffic gets to your IBMi there should be various layers in place, for arguments sake there should be security on all of your connections to the internet - so your hub connecting you to the internet should have as much security and monitoring on it as possible - you should look at these logs very frequently. This hub will protect all the devices configured on your local network.
When hopefully, most of the traffic is filtered out, the traffic hitting your IBMi should only be from your internal network and traffic that has been specifically allowed through the hub which should ideally be SSH or VPN traffic.
Protection on the IBMi should still be monitored and here is how to start your security on IBMi using Enforcive.
The firewall manager on Enforcive has three groups:
- Outgoing Rules
- Incoming Rules
- Port Listening Rule
Outgoing Rules limit the traffic leaving the IBMi. This is just as important to ensure that nothing is configured that sends information out that you don't know about. Rules are configured to log successful events and un-successful events. Successful events conform to your rules un-successful do not.
Incoming Rules limit the traffic entering the IBMi. This is probably where you start configuring your protection. Rules are configured to log successful events and un-successful events.
Port Listening Rules define what ports can be activated on the IBMi and for the logging of activation attempts.
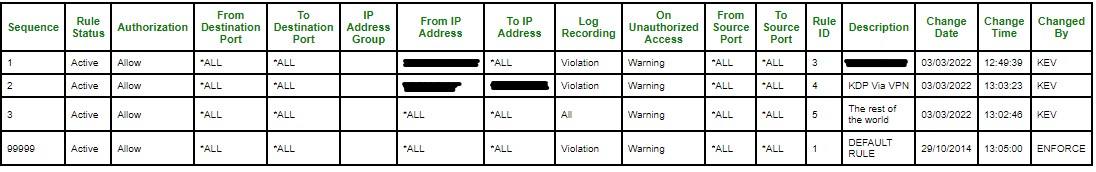
What's configured:-
- From destination port
- To destination port
- From Source IP address
- To Source IP address
- Log Recording (violation or all)
- On Unauthorised Access (warning or reject event)
- Rule Description
- From Source Port
- To Source Port
Enforcive then processes each rule in turn, if the event matches the rule then the event is processed and further processing stops.

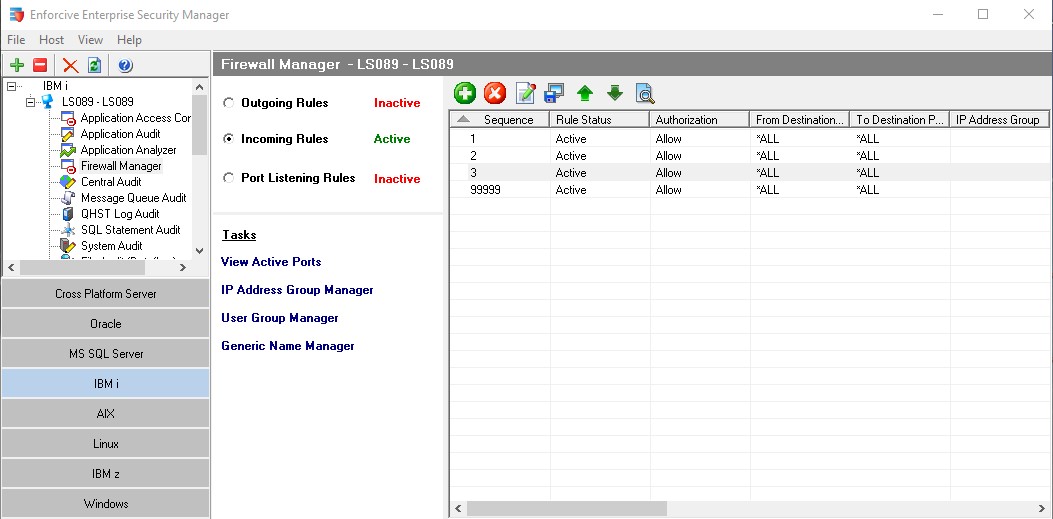
In my configuration I am logging all access that appears after rule 2. When I am happy I can change the access control to REJECT.
Layer Summary
Layer 1 The first layer of security is our service providers hub making the connection to the internet - that restricts traffic to our IBMi from their local network.
Layer 2 is our Enforcive firewall software on the IBMi.
From the image above our rules are set as follows:-
- sequence 1 allows a specific IP from our service provider
- sequence 2 allows a range configured for our VPN
- sequence 3 monitors the rest of the world logging all access as a warning (I also have an immediate alert set up if any access comes in via this rule). Once tested I will set 'On Unauthorized access' to REJECT. Note: our service providers layer 1 blocks all traffic anyway. This adds another layer of protection.
Layer 3 is configured with Enforcive application security and is configured for the following services.
- FTP client
- FTP Server
- Telnet
- Signon server
- Database server
- RMTSQL
- DDM
- Data queue
- Pass Through
- File transfer
- File Server (IFS)
- DRDA
- Central server
- Network print
These services are also configured to allow specific access, monitoring and alerting.
If you would like more information regarding Enforcive and how you can protect your IBMi and its services contact me, Kevin Passey via the Contact Page of this website.



